Countermeasures Against Cyber Attacks
1.Countermeasures Against Cyber Attacks
The Kirin Group has established the following frameworks and initiatives to respond to the recent rise and advancing sophistication of cyber attacks.
-
Established KIRIN-CSIRT (Computer Security Incident Response Team), a dedicated team responsible for early detection of security incidents, prompt initial response, and thorough root cause analysis to minimize potential damage.
-
In coordination with the Security Operation Center (SOC), we have deployed security tools with machine learning capabilities to enhance automated incident detection and rapid response.
-
We have established a multilayered defense using a range of tools to detect and block threats, thereby preventing potential business disruption and information leakage.
-
We have implemented global risk-transfer measures, including adopting cyber insurance.
2.Basic Policy on Information Security
The Kirin Group recognizes information security as a critical risk and has established systematic measures based on the following three pillars:
-
1.Establishment of internal rules and thorough employee training
-
2.Strengthening governance within the Group
-
3.Promotion of technical measures
Based on these pillars, we have developed Group-wide ‘Information Security Regulations’ and various manuals, adopting a rule system compliant with ISO/IEC 27001 (JIS Q 27001), which is regularly reviewed and updated as needed.
Furthermore, we have established a ‘Privacy Data Protection Policy’ aligned with global standards, and are promoting compliance with the OECD’s eight principles and relevant laws and regulations in each country.
Information Security Structure
-
The Kirin Group's information security structure balances the assignment of personnel in charge at each location with an integrated governance structure for the entire Group.
-
Information security managers are assigned to each operating company to establish, maintain, and manage the system by delegating authority.
-
The Group Risk and Compliance Committee plays a central role in identifying and assessing risks across the entire company and identifying critical risks.
-
Appoint information security managers at domestic and overseas bases (factories, sales offices, laboratories, etc.)
-
Kirin Holdings' Digital ICT Strategy Department serves as the company-wide department responsible for overseeing and promoting information security.
Information Security Governance Framework
In addition to clarifying the frameworks for initiatives regarding information security measures and reducing the risks of leaks of information assets, we will respond to external threats against information security and enhance effectiveness of information security measures.
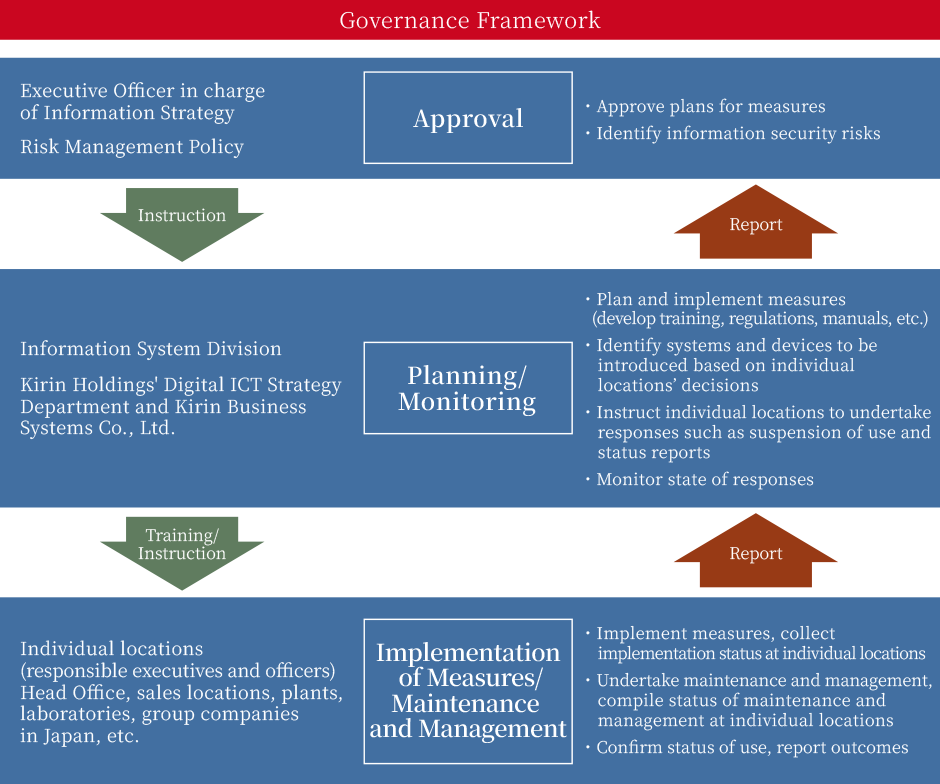
Information Security Promotion Framework
Information security promotion staff will play the central role in the promotion of information security.
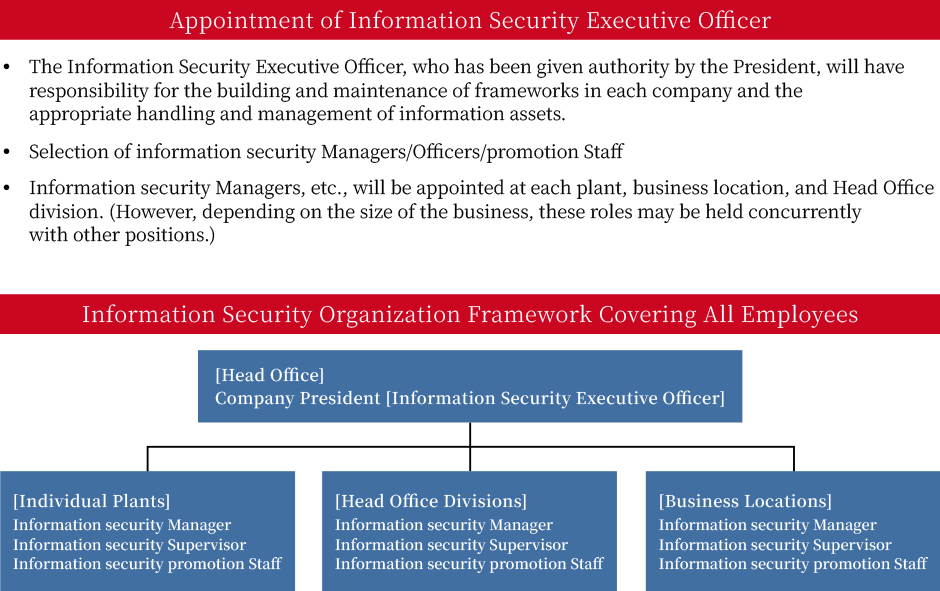
Information Security Initiatives
The Kirin Group considers information security to be a fundamental issue underpinning its corporate activities and is implementing multifaceted measures across technical, human, and physical domains. These measures are positioned not merely for risk avoidance but as the foundation for sustainable growth and reliable corporate operations.
Education and Human Resource Development
-
Provide company-wide e-learning to ensure all employees acquire essential information security knowledge.
-
Deliver phased training for approximately 400 information security managers, progressing participants from basic awareness to practical, action-ready competency.
-
Operate KISeP (Kirin Security Portal) to support repeated learning, consultation, and information sharing.
Technical measures
-
Apply robust security controls to smart devices.
-
Reduce risks associated with outsourcing and cloud services through usage policies, contract management, and communication/network controls.
Physical measures
-
Maintains strict access control for facilities.
-
Publish remote-work guidelines to address risks such as inadvertent disclosure and unauthorized viewing (shoulder surfing).
-
Provide checklist-based reminders to ensure secure practices are maintained in remote environments.